It has been more than a decade since Bitcoin was created and launched. Over the years, the blockchain revolution has attracted some of the brightest minds in the world working to improve on Bitcoin technology.
One of the most important areas that Bitcoin has an obvious limitation is anonymity and privacy. It is arguable that most of the people that use Bitcoin need this feature more than any other and so some blockchain projects have borrowed what is lauded about the grandfather of blockchain networks has to offer and innovated to introduce privacy. One of the leading projects pushing for privacy in blockchain networks is Zcash.
Zcash was introduced in early 2016 utilizing the bullet-proof communication protocol called Zerocash which uses zk-Snarks. This allowed transactions on the Zcash blockchain to remain private by obfuscating the sender and the amount of the transaction.
As innovative as this was, the Zcash implementation was also limited to some extent as the community only applied the zk-SNARKS technology to cryptocurrency transactions.
A faction of the ZEC community felt that Zcash could be so much more and this led to the birth of Hush. Hush was initially called ‘ZDash,’ a name I later ditched. It was forked off the Zcash 1.0.9 codebase.

Move towards Communication
The main reason that saw Hush fork from Zcash was to bring the class-leading privacy technology to communication. Hush is still a cryptocurrency but on top of that, it is a communication protocol.
Since its launch in November 2016, the Hush community has innovated on ways to bring privacy and anonymity in communication. Sending messages between two or more people has become a basic component that most people don’t even care about their privacy. Government agencies have taken advantage of this and now use these channels to track and snoop on people.
Hush now focuses on solving this problem. It is concentrated on private messaging and smart contracts. By utilizing zk-SNARKS technology, Hush now offers one of the leading channels of communication that promotes privacy and anonymity.
The community has built two clients – Hush Messenger and Hushlist – which employ the zero-knowledge proof technology to enable private communication. Also, Hush has infused zk-SNARKS into its flagship mining client SilentDragon enabling its users to both send and receive private messages. SilentDragon is also a mining platform and wallet.
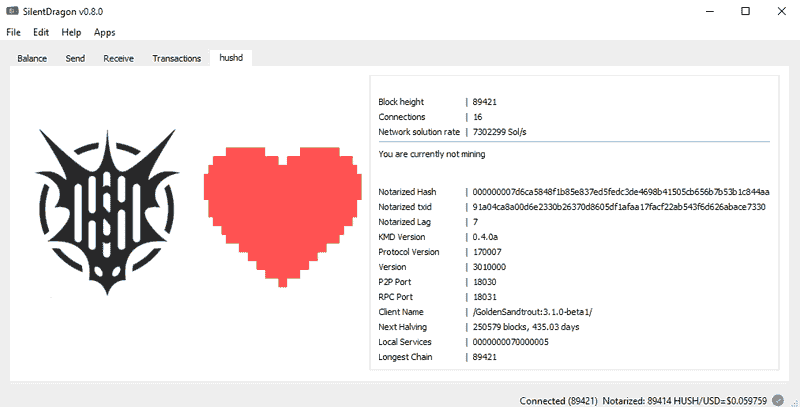
Technology
Any blockchain is as good as the technology behind its network and a solid blockchain adheres to three principles – speed, security, and decentralization.
All these three aspects culminate in the most fundamental feature of a public blockchain and that is consensus. It is defined as how a blockchain is built and how blocks are confirmed.
Initially, Hush used the bitcoin consensus mechanism called Proof of Work. However, despite the similarity in the consensus mechanism, Hush employed a different hashing algorithm called Equihash as opposed to Bitcoin’s SHA-256. The downside of using SHA-256 was that it encouraged the use of application-specific integrated circuits (ASICs) which are expensive and led to the centralization of mining.
Hush borrowed the Equihash mining algorithm from the Zcash codebase. Equihash has been implemented in some of the leading blockchains including the Komodo Platform, Bitcoin Gold, and Zencash.
Equihash is anti-ASICs meaning that the network can mitigate against the introduction of more powerful machines and therefore impeding the case for decentralization. However, since Hush was a small project, it was susceptible to security attacks more commonly called 51% attacks. In a 51% attack, a malicious player accumulates a majority of the hashing power which then means that they control the creation of blocks.
To protect against this attack, Hush migrated to the Komodo network in January 2019. Komodo uses a novel consensus mechanism called delayed proof of work (dPoW) in which it notarizes network data to the most secure blockchain –bitcoin.
This setup allows Hush nodes to still confirm their transactions and then notarize the resultant blockchain data onto the Komodo platform which in turn also has nodes that confirm these transactions.
Once the transactions are confirmed, notary nodes then notarize the data onto the bitcoin blockchain. dPoW allows a blockchain such as Hush to inherit Bitcoin-level security at launch time without spending useful resources on onboarding more nodes to the network.
Get involved
The Hush community is created based on the open-source ethos. Anyone can join and contribute as long as they offer positive insights. The community maintains a GitHub repository accessible to anyone.
Hush coins are also easily available on the Komodo affiliated decentralized exchange AtomicDEX and BarterDex. You can swap your coins against several pairs including Komodo’s KMD, Bitcoin [BTC], and Tether stablecoin [USDT] among other pairs.
Links of interest
- Web: https://myhush.org
- Telegram: https://t.me/Hush_Coin
- Twitter: https://twitter.com/MyHushTeam
- Discord: https://discordapp.com/invite/QGPdzxH