TL;DR
- Matcha Meta confirmed an exploit in its SwapNet integration that resulted in estimated losses of $16.8 million and affected a specific set of wallets.
- PeckShield detected the anomalous activity, and CertiK identified an arbitrary call vulnerability in the SwapNet router that enabled unauthorized transfers.
- The attacker swapped $10.5 million in USDC for 3,655 ETH on Base and used a bridge to move the funds to Ethereum; Matcha suspended SwapNet and revoked its permissions.
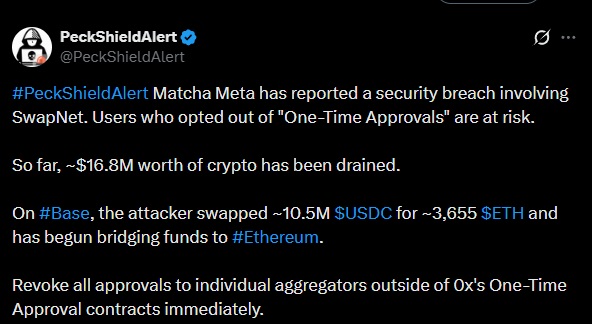
Matcha Meta confirmed a security incident linked to its integration with SwapNet that led to estimated losses of $16.8 million. The episode was limited to a specific subset of users and did not compromise the entire wallet base of the DEX aggregator.
The initial alert came from the security firm PeckShield, which detected anomalous activity associated with SwapNet contracts. CertiK later published a technical analysis that identified a specific vulnerability in the design of the router used by the integration. The issue originated from an arbitrary call flaw within the SwapNet contract, which allowed the execution of unauthorized calls.
The exploit exclusively affected users who had disabled Matcha Meta’s One-Time Approval feature. By choosing that configuration, those wallets granted persistent permissions directly to the SwapNet router instead of approving each transaction individually. That approval structure enabled fund transfers without additional per-transaction validation.
According to on-chain data reviewed by the security firms, the attacker executed swaps totaling approximately $10.5 million in USDC on the Base network. From those operations, the attacker obtained around 3,655 ETH. The assets were later transferred via a bridge to the Ethereum network. The movements were carried out across multiple transactions and through intermediary contracts.
Matcha Suspended SwapNet-Related Contracts
The scope of the incident was limited to wallets that maintained active direct approvals on the SwapNet router. Users who retained the one-time approval scheme did not record losses. Matcha Meta stated that the rest of the aggregator’s infrastructure did not exhibit additional failures during the event.
After confirming the exploit, Matcha Meta immediately suspended the contracts linked to SwapNet. The platform requested that users manually revoke existing approvals, with a focus on the identified router. In parallel, it removed the option to disable the one-time approval system from its interface.
There have already been recorded cases of exploits associated with routing contracts and persistent permissions in decentralized aggregators. Beyond relying on platforms, each user is required to manage their own layers of protection