TL;DR
- A new wave of front-end attacks and exploits targeted the DeFi projects OpenEden, Curvance, and Maple Finance, compromising their websites.
- OpenEden identified the wallet drainer AngelFerno as responsible and blocked interactions on its domains, while Curvance reported a domain exploit without a DNSSEC signature.
- Scam-as-a-service scripts, such as AngelFerno, allow malicious transactions to be generated based on the assets in the victim’s wallet, distributing profits between the developer and the attacker.
A new wave of front-end exploits has affected several DeFi projects, putting millions of users at risk. The platforms OpenEden and Curvance were attacked this Monday, while Maple Finance suffered a similar incident last week. The attacks involve compromising project websites and inserting malicious code that prompts users to unintentionally transfer their assets to attackers.
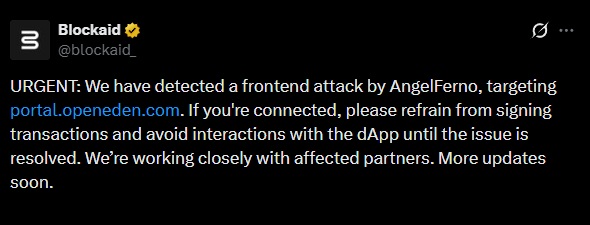
The attack on OpenEden was reported by the security firm Blockaid. The company urged users not to sign transactions or interact with the dApp until the issue was resolved. OpenEden identified the wallet drainer AngelFerno as responsible and warned users of openeden.com and portal.openeden.com that using these pages could result in asset loss. The project provided a link to its proof of reserves to confirm that the underlying assets remain secure.
Heavy Blows to the DeFi Sector
Hours later, Ethereum Security Alliance member “pcaversaccio” reported a domain exploit affecting the lending platform Curvance’s website. The domain had been updated without a DNSSEC signature, and a malicious approvals transaction apparently generated by AngelFerno was detected. Curvance stated that preventative measures were taken before any funds were lost and advised users to refrain from interacting with the front-end until further notice.
Maple Finance suffered a similar attack last week. The platform, an on-chain asset manager with $2 billion under management, reported that it regained control of its site and confirmed that smart contracts and funds remain secure and unaffected.
Exploits Using Automated Scripts
AngelFerno and other scam-as-a-service scripts allow attackers to generate malicious transactions based on the assets present in the victim’s wallet. The scripts are distributed to phishing attackers and SIM swappers, and any proceeds are automatically split between the drainer developer and the executing attacker.
Deception methods include fake airdrops, spoofed front-ends, and fraudulent security alerts. Victims have not only been inexperienced users; even some hackers have been affected by these attacks.
The wave of front-end exploits continues to pose a direct threat to DeFi users. The affected platforms have implemented security measures and maintain protection for funds and smart contracts, but users must remain vigilant and avoid interacting with compromised front-ends until the issues are fully resolved.