TL;DR
- Ledger suffered a new data breach through its payment processor Global-e, exposing customers’ names and contact information.
- The incident was detected by Global-e and mitigated immediately. Independent forensic experts are currently investigating it.
- The breach leaves users exposed to phishing attacks and social engineering threats.
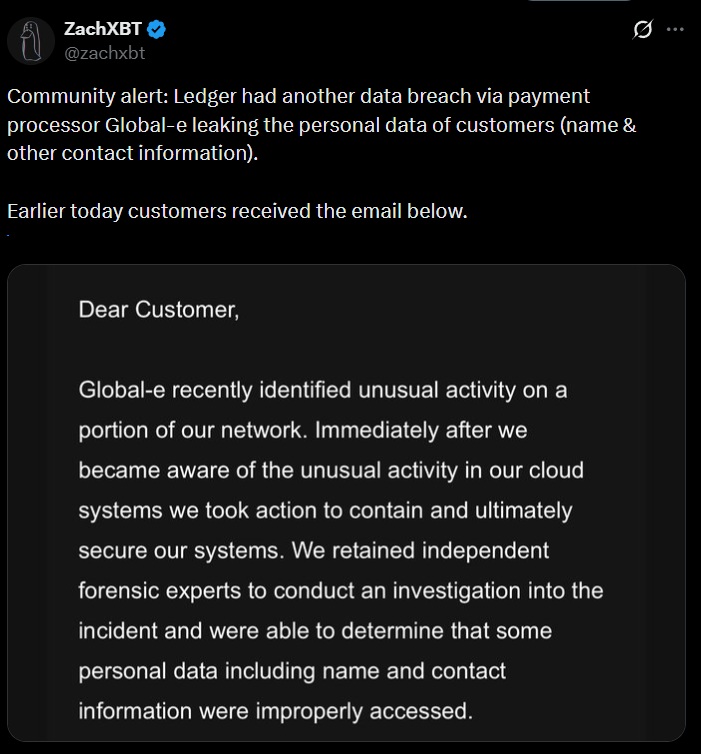
Ledger experienced another data breach via its payment processor Global-e. The incident exposed customers’ names and contact details but did not compromise private keys, wallet firmware, or on-chain assets. The breach was reported by on-chain researcher ZachXBT, who highlighted the vulnerability in Ledger’s external service providers.
The issue was discovered when Global-e identified unusual activity in part of its network. The company acted quickly to contain the breach and secure the affected systems. Independent forensic experts are investigating the scope and cause of the incident. Customers began receiving emails explaining that certain personal data had been improperly accessed and that mitigation measures were applied immediately.
What Happened?
The breach did not originate from Ledger’s core infrastructure but through its external provider. Global-e handles payments and checkout services. This is one of the most common problems in the hardware wallet industry: vulnerabilities often lie not in the company’s software or hardware but in third-party partners processing off-chain data. ZachXBT noted that this pattern has repeated in other cases, making external providers the weakest link in security.
Although customers’ funds remain safe, the exposure of personal data leaves them vulnerable to phishing campaigns, identity theft attempts, and social engineering attacks. Security researchers warn that attackers often combine leaked information with fake support messages or fraudulent wallet update requests to trick users into revealing their recovery phrases.
Ledger Advises Extra Precautions
Ledger and Global-e recommend that users take all possible precautions: distrust unsolicited emails, calls, or messages claiming to be official, avoid clicking links or downloading files from unexpected communications, and never share private keys or recovery phrases. Official channels and verified domains should be the only sources for updates or support.
The investigation remains ongoing, and so far, there is no evidence of further data leaks beyond the personal information of some customers