TL;DR
- A governance failure in Unleash Protocol allowed an attacker to steal $3.9 million without compromising the underlying blockchain or raising immediate alarms.
- The attacker exploited the multisig system to execute an unauthorized contract upgrade, bypassing controls and moving funds directly.
- After the attack, the funds were fragmented and sent to Tornado Cash. Unleash paused operations and is reviewing its governance processes and key management practices.
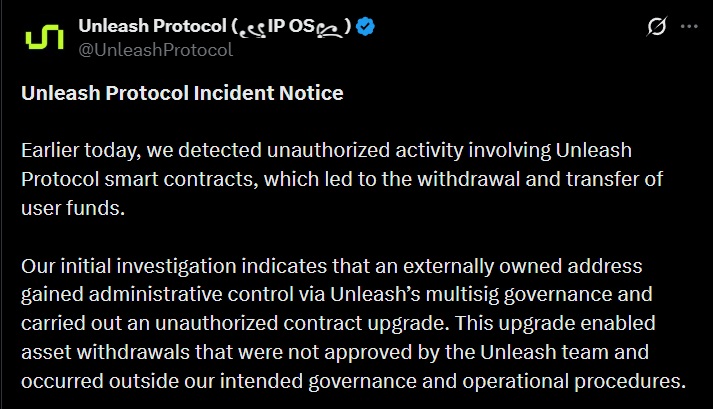
A governance failure in Unleash Protocol enabled an attacker to steal $3.9 million in user funds. The incident did not compromise the underlying blockchain or Story Protocol validators but highlighted how vulnerabilities in contract administration can lead to significant losses.
How the Attack Worked
The attack originated in Unleash’s multisig system. The attacker obtained administrative permissions normally requiring approval from authorized signers and used them to execute an unauthorized contract upgrade. This change altered how withdrawals were processed, bypassing any governance controls and allowing the attacker to move funds directly out of the protocol.
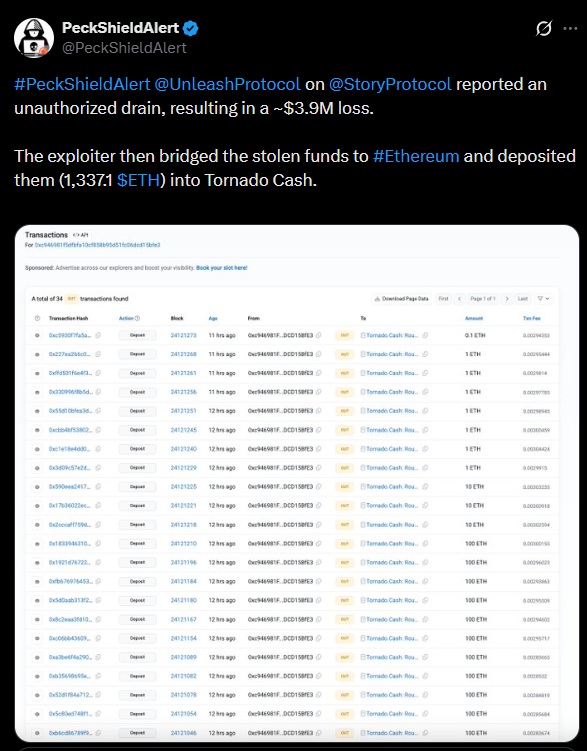
Affected assets included WIP, USDC, WETH, stIP, and vIP. All withdrawals occurred through the altered contract rather than normal user interactions. After extraction, the funds were transferred to Ethereum and split across multiple transactions. A total of 1,337.1 ETH was deposited into Tornado Cash, a deliberate attempt to obscure the trail and hinder on-chain monitoring.
Unleash responded immediately by pausing all operations to prevent further losses. The team is now working with forensic and security experts to understand how governance protections were bypassed. They are reviewing multisig signer activity, key management, and internal contract administration processes. Users were advised not to interact with the contracts until further official instructions are issued.
Governance systems can become points of weakness. Even if the base blockchains are secure, permission management and contract upgrades in decentralized applications remain vulnerable. Internal controls, contract update procedures, and signer oversight are as critical as the security of the underlying network.
Unleash Continues Investigating
Unleash also emphasized that the investigation remains ongoing and that any final conclusions will be communicated through official channels. This episode underscores that decentralization does not inherently guarantee safety. Weak governance, unsupervised upgrades, and concentrated permissions can cost millions.
Security depends not only on the base code but on the control and management of every layer of the application. Without active oversight, any decentralized protocol can become an easy target