TL;DR
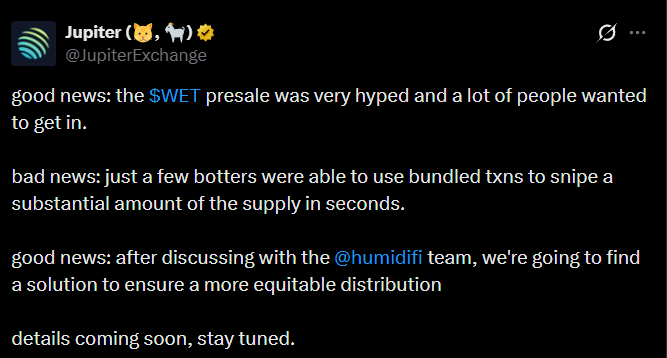
- The WET token presale on Solana was scrapped after a Sybil attack in which a bot farm used more than one thousand wallets to capture the supply.
- HumidiFi canceled the launch, created a new token, and announced an airdrop for valid buyers, excluding the attacker.
- Analytics firm Bubblemaps traced the activity and linked it to a single entity that controlled more than 1,100 wallets funded within an identical time window.
The WET token presale on Solana was canceled after a bot farm used more than one thousand wallets to capture nearly the entire supply in an attack that lasted only a few seconds.
What Happened With WET?
The event, organized by the AMM HumidiFi and executed through the Jupiter aggregator, sold out instantly, but legitimate buyers had no chance to enter. The team confirmed the attack, canceled the launch, and announced a new token along with an airdrop for valid participants. The attacker will be excluded from the process.
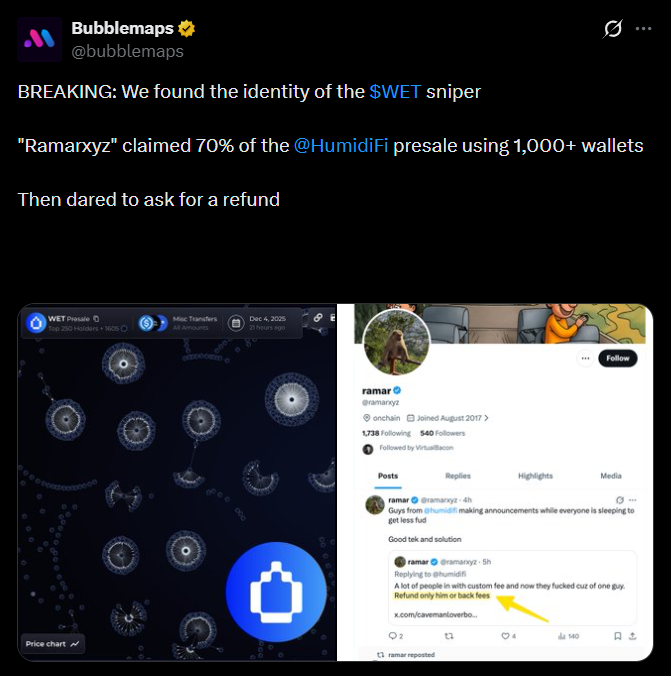
Analytics firm Bubblemaps reviewed participation patterns and linked the attack to a single entity that controlled at least 1,100 of the 1,530 wallets involved. The analysis detected a cluster of wallets with no prior on-chain history, all funded by a small set of addresses within a narrow time window and with similar amounts in SOL and USDC.
This structure revealed repetitive behavior that allowed analysts to group movements and trace indirect connections. One of the clusters leaked enough data to link the activity to an account called Ramarxyz, who even appeared requesting a refund.
The alleged attacker had reportedly funded thousands of new wallets from exchanges that had received 1,000 USDC before the presale. This pattern showed an automated process that replicated deposits, movements, and entry times, a typical sign of Sybil attacks that aim to take control of initial sales or airdrops.
Sybil Attacks Are Evolving
The incident adds to other recent cases. In November, a single entity captured 60% of aPriori’s APR token airdrop. Days later, a set of wallets linked to Edel Finance took 30% of the EDEL supply during the launch. The firm denied manipulating the distribution and said the tokens were locked in a vesting contract. Even so, the repeated episodes confirm a pattern increasingly affecting projects that run open sales.
Bubblemaps CEO Nick Vaiman said Sybil attacks are evolving and require stricter controls. He suggested that teams adopt KYC verification processes or algorithmic systems that detect anomalous clustering before token allocation. He also recommended manually reviewing participant lists when demand exceeds supply and automation signals become evident.
HumidiFi will resume the public sale on Monday with a new distribution and an explicit filter against the attacker. The team aims to restore credibility and protect buyers who were excluded from the original process