TL;DR
- SlowMist detected a phishing campaign that imitates MetaMask’s security and induces users to hand over their seed phrase during a fake 2FA verification.
- In 2025, phishing losses fell 83% to $83.85 million, but attackers moved away from large-scale heists and shifted toward mass campaigns targeting retail users.
- MetaMask, Phantom, WalletConnect, and Backpack activated a network with SEAL that validates reports and blocks phishing attacks in real time.
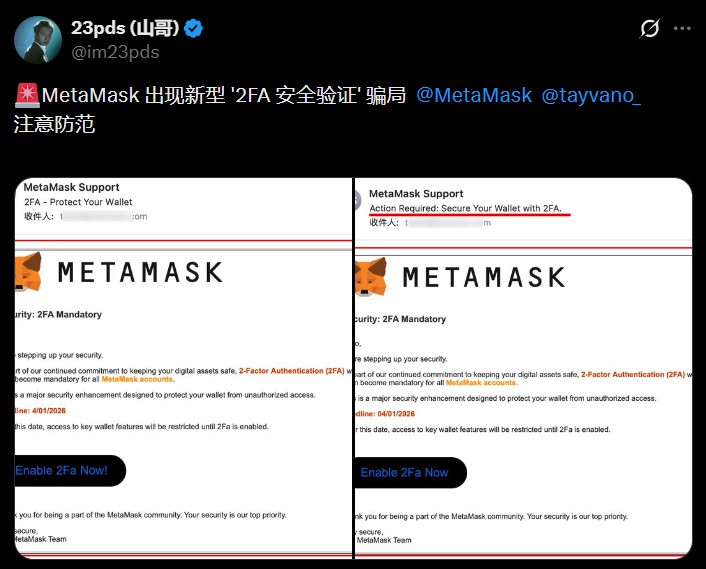
SlowMist detected a phishing campaign that impersonates MetaMask’s security mechanisms to steal recovery phrases and take full control of wallets. The scam does not rely on malware or technical vulnerabilities. It is built on design, timing, and trust. The goal is to push users to enter their seed phrase while believing they are completing a legitimate verification process.
The scheme starts with fake domains that are almost identical to the original, featuring minimal spelling variations of “metamask.” From there, the victim is redirected to a page that replicates the wallet’s security interface. The design, colors, and language match MetaMask’s real flows. At first glance, there are no obvious warning signs.
Fewer Large Heists
The next step presents a supposed 2FA verification screen. Timers appear alongside warning messages and asset protection reminders. Every element is designed to reinforce a sense of legitimacy. The final step asks for the recovery phrase under the pretext of completing the validation. At that point, the wallet is automatically compromised and the funds move to the attacker.
Phishing losses in 2025 dropped 83% to $83.85 million, down from nearly $494 million the previous year. The number of affected users fell to around 106,000, a 68% year-over-year decline. Even so, attackers refined their approach. Fewer large hits, more targeted campaigns aimed at retail users.
MetaMask and Other Wallets Join Forces to Slow Hackers
The third quarter recorded the highest volume of losses, with $31 million during the strongest phase of Ethereum’s rally. August and September accounted for nearly 29% of the annual total. The largest single theft reached about $6.5 million and relied on a malicious Permit signature.
Permit and Permit2 approvals were responsible for 38% of losses in cases above $1 million. Following Ethereum’s Pectra upgrade, new EIP-7702 signature exploits emerged, allowing multiple harmful actions to be bundled into a single user approval. Two incidents in August resulted in $2.54 million in losses.
MetaMask, Phantom, WalletConnect, and Backpack launched a global phishing defense network with SEAL that validates reports and distributes them in real time across different wallets. The system aims to shorten the gap between detection and blocking. Losses declined, but the issue remains active. Phishing does not disappear, it adapts