TL;DR
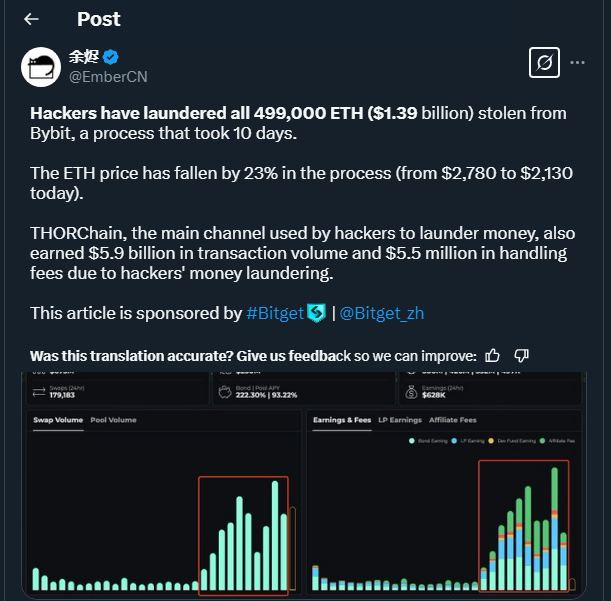
- Lazarus Group successfully laundered 499,000 ETH stolen from Bybit, valued at $1.39 billion, in just 10 days, causing Ethereum’s price to drop by 23%.
- THORChain processed over $5.9 billion in transactions for the hackers, collecting $5.5 million in fees, making this the largest crypto laundering case in history.
- Bybit launched a bounty program with up to $140 million available to recover stolen funds and strengthen blockchain ecosystem security.
The North Korean hacker group Lazarus Group has managed to launder all 499,000 ETH stolen from the Bybit exchange platform in a record time of just 10 days. According to EmberCN’s analysis on X, this massive movement of funds had a significant impact on the market, driving Ethereum’s price down from $2,780 to $2,130, a 23% drop. Despite efforts from the crypto community, blockchain analysts, and global authorities, the assets have been scattered across multiple wallets and are virtually unrecoverable.
Did Bybit’s Bounty Plan Fail?
In response to the attack, Bybit launched an unprecedented bounty program, offering up to $140 million to anyone providing useful information on the whereabouts of the stolen funds. However, so far, only small amounts have been recovered. Bybit’s CEO, Ben Zhou, stated that the initiative will not stop until Lazarus is neutralized and announced the creation of HackBounty, a collaborative platform aimed at combating future threats in the industry.
THORChain and Decentralization Under Scrutiny
One of the most striking aspects of this case is the role of THORChain, a decentralized platform that enabled hackers to move $5.9 billion in transactions while earning $5.5 million in fees. This situation has reignited the debate on security in decentralized exchanges (DEX) and their potential use for money laundering. While some see this as a vulnerability, others argue that decentralization is precisely what makes the crypto ecosystem resilient.
What Happened in the Bybit Hack?
The attack took place on February 21 at 12:30 UTC, when the funds were moved from a cold wallet to a hot wallet. Lazarus exploited a vulnerability in SafeWallet, an asset management software used by Bybit. Researchers from Sygnia Labs and Verichains determined that the attackers modified the platform’s JavaScript code, allowing them to redirect funds into their own wallets.

Additionally, it is suspected that the security breach originated from an attack on Bybit’s cloud infrastructure, possibly through AWS S3 and CloudFront.
This incident offers several important lessons for the whole crypto community. While decentralization provides significant advantages, it also presents challenges in terms of security and fund recovery.