In 2025, attackers drained billions of dollars from Web3 wallets. In most cases, the underlying blockchain infrastructure was not compromised. Instead, losses occurred because users unknowingly approved malicious smart contract interactions.
Hardware wallets protect private keys, and antivirus software helps prevent traditional malware. However, neither is designed to interpret smart contract logic. When a user signs a transaction, a wallet confirms the signature request, not the intent behind it.
This highlights a structural difference between traditional digital security and Web3 security. Blockchain transactions are transparent but irreversible, and malicious contracts can appear legitimate at first glance. As a result, Web3 requires security tools specifically designed to analyze on-chain behavior before transactions are executed.
This guide outlines key Web3 security tools relevant in 2026 and explains how they address risks unique to blockchain environments.
Why Web3 Security Is Different
Web3 security differs fundamentally from traditional online security models. Understanding these differences is essential for managing digital assets safely.
Hardware wallets have limited scope
Hardware wallets such as Ledger or Trezor secure private keys from external compromise. However, they do not evaluate transaction intent.
If a user approves a malicious transaction, the wallet processes the request as instructed. The device secures access, but decision-making remains the user’s responsibility.
Blockchain transactions are irreversible
Unlike traditional banking systems, blockchain transactions cannot be reversed. Once a transaction is signed and confirmed, assets are transferred permanently. This makes pre-transaction analysis especially important in Web3 environments.
Traditional antivirus software is insufficient
Antivirus tools are designed to detect known malware patterns in files and executables. They do not interpret smart contract code or blockchain permissions.
Understanding functions such as token approvals or asset transfers requires tools that are aware of blockchain-specific risks.
Essential Web3 Security Tools
The following tools focus on preventing common Web3-related threats by analyzing contracts, permissions, and transaction behavior before execution.
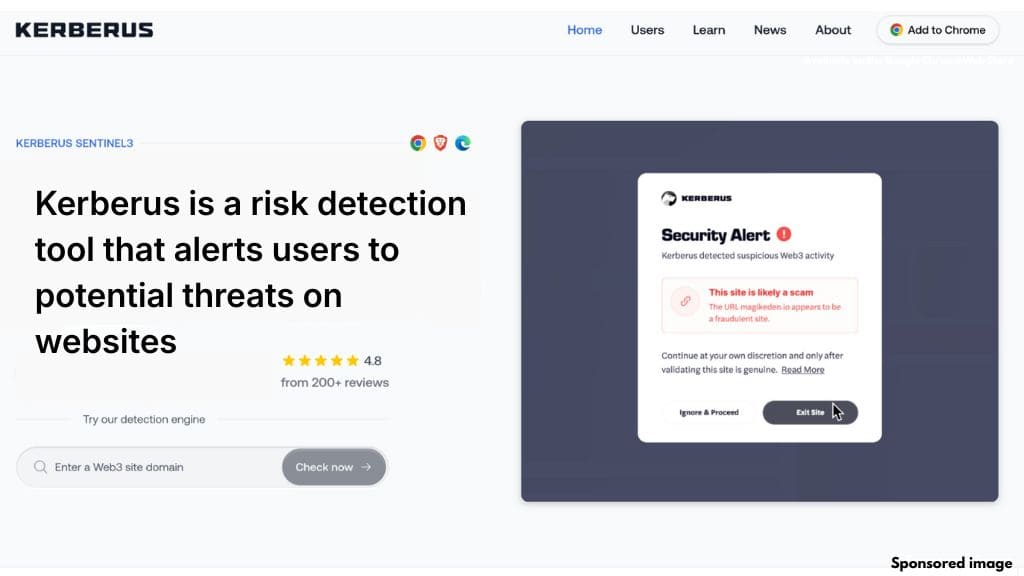
1. Kerberus
Kerberus is a browser-based security tool designed to analyze smart contracts and decentralized applications in real time. It uses an AI system called Sentinel3 to scan websites and contracts before wallet connections are approved.
Rather than relying solely on static blocklists, Sentinel3 evaluates behavioral patterns to identify previously unseen threats. This approach allows it to flag potential risks even when contracts have not yet been widely reported.
Kerberus supports over 1,000 EVM-compatible networks and has expanded coverage to Solana. The extension operates in the background and only alerts users when potential issues are detected.
The platform also offers transaction coverage through the Fairside network, providing an additional layer of protection in certain scenarios. Advanced features are available through its premium offering.
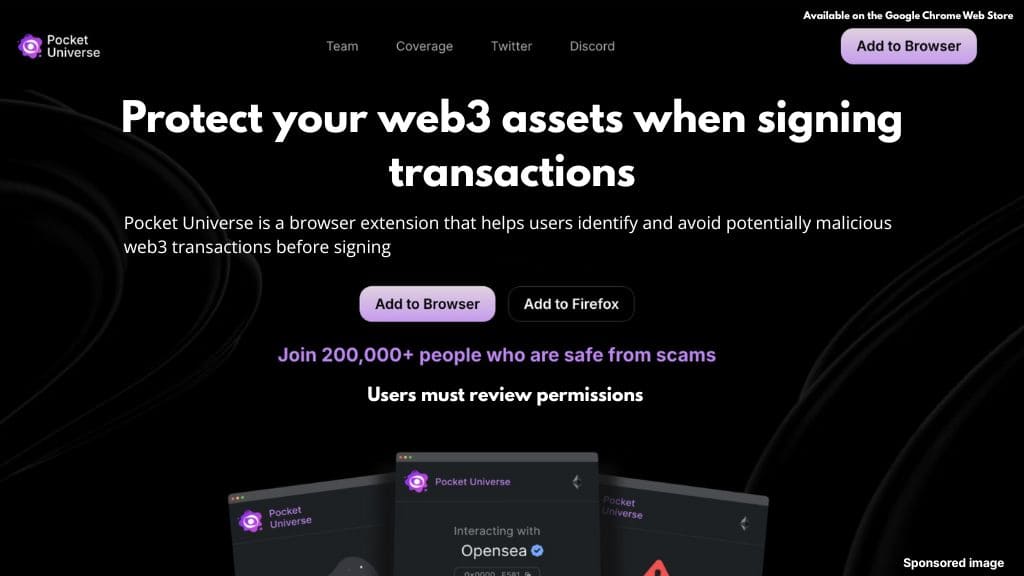
2. Pocket Universe
Pocket Universe focuses on transaction transparency. Before a transaction is signed, the tool simulates its execution on a forked version of the blockchain. This allows users to preview outcomes without risking funds.
The results are displayed in clear language, outlining asset movements and permission changes. This helps users understand exactly what a transaction will do, including whether it grants ongoing access to tokens or NFTs.
Pocket Universe is effective at identifying common exploit patterns such as permission abuse, signature-based NFT drains, and restrictive token contracts. Its transaction preview functionality is designed to reduce approval-related errors.
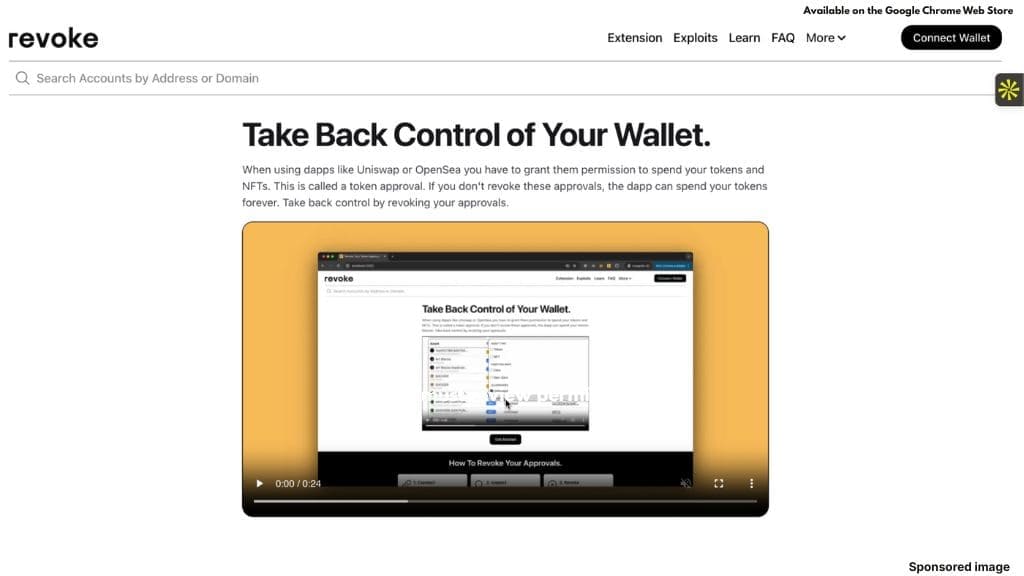
3. Revoke.cash
Revoke.cash addresses risks associated with token approvals. Many decentralized applications require users to grant spending permissions, which often remain active indefinitely.
The platform displays all active approvals associated with a wallet, including older permissions that may no longer be needed. Users can revoke or limit these approvals to reduce exposure.
Revoke.cash supports a wide range of blockchains and Layer 2 networks. Its browser extension can also warn users before signing unlimited approvals, encouraging more controlled permission settings.
4. Web3 Antivirus
Web3 Antivirus evaluates smart contract code and assigns risk indicators based on its structure and functionality. It highlights features such as upgradeable proxies, blacklist functions, or patterns associated with known exploits.
For NFT and token traders, the tool can help identify contracts with restrictive selling conditions or suspicious trading behavior. Machine learning models compare new contracts against historical exploit data to flag similarities.
This type of analysis is particularly useful when interacting with newly launched tokens or lesser-known protocols.
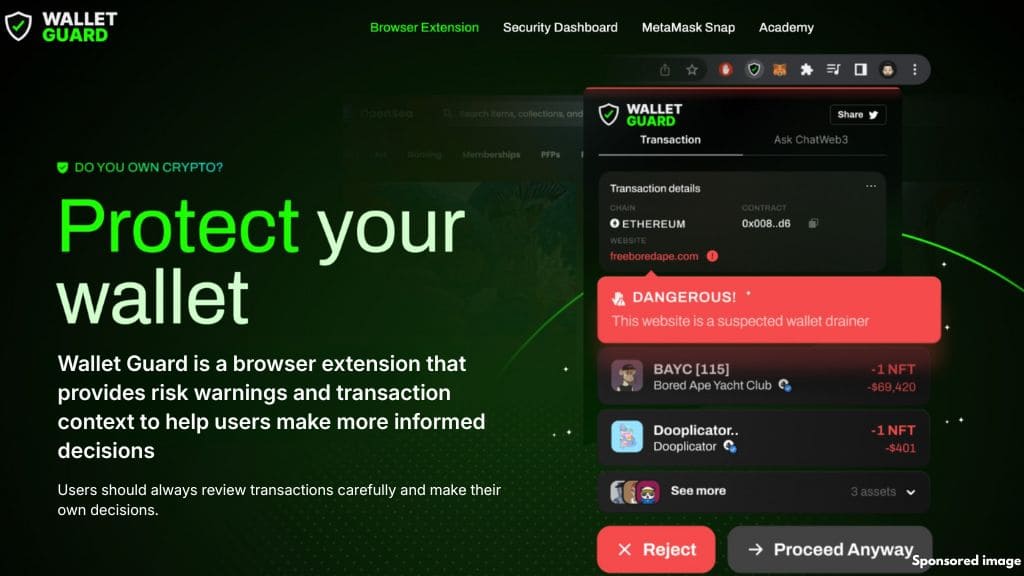
5. Wallet Guard
Wallet Guard focuses on browser-level protection. It monitors websites and extensions for hidden scripts that may activate during wallet connections.
Its Storm Detection feature identifies malicious code embedded in otherwise legitimate-looking sites. The platform also provides a dashboard that summarizes wallet risk factors, including outdated approvals and past high-risk interactions.
Wallet Guard maintains an actively updated phishing database and integrates alerts directly into the browsing experience, blocking access before interaction occurs.
Conclusion
Web3 security has evolved beyond simple blocklists and manual checks. Modern threats require tools that can analyze smart contracts, permissions, and transactions in real time.
Traditional security software does not address the unique risks of decentralized systems. Specialized Web3 tools help bridge this gap by providing transaction previews, approval management, and contract analysis before irreversible actions occur.
A layered approach remains the most effective strategy. Combining real-time threat detection, transaction simulation, and regular permission reviews can significantly reduce exposure to common Web3 risks.
As blockchain ecosystems continue to expand, security tools must adapt alongside them. Understanding and applying the right protections is an essential part of participating safely in Web3 environments.
Press releases or guest posts published by Crypto Economy have been submitted by companies or their representatives. Crypto Economy is not part of any of these agencies, projects or platforms. At Crypto Economy we do not give investment advice, if you are going to invest in any of the promoted projects you should do your own research.