TL;DR
- Security firm CertiK detected the movement of these funds linked to illicit activities attributed to the North Korean hacker group.
- Six malicious packages have been identified within the NPM ecosystem, aiming to steal credentials and extract crypto-related data.
- The methods used align with previous attacks, confirming the continuous evolution of their operations within the crypto ecosystem.
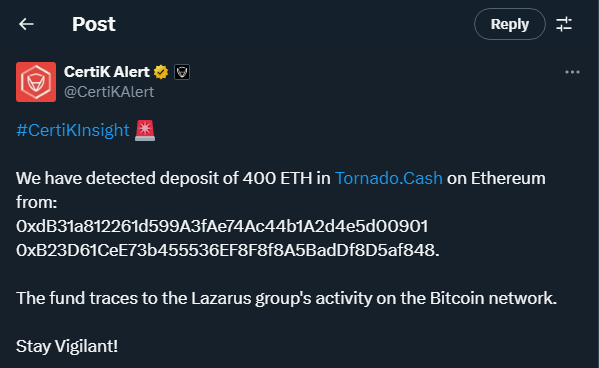
Blockchain security firm CertiK has raised an alert about a new financial transaction linked to the Lazarus Group, the infamous hacking collective associated with North Korea. A deposit of 400 ETH, valued at approximately $750,000, was detected in Tornado Cash, a cryptocurrency mixer that allows funds to be obscured.
This group is responsible for some of the largest thefts in cryptocurrency history, including the attack on the Bybit exchange platform on February 21, in which they managed to steal $1.4 billion in digital assets. They are also linked to the hack of Phemex in January 2024, where $29 million was lost.
Over the years, Lazarus has been accused of carrying out some of the biggest cyberattacks in the crypto industry, including the $600 million theft from the Ronin network in 2022. Data from security firm Chainalysis reveals that in 2024, North Korean hackers have stolen over $1.3 billion in 47 attacks, doubling the figures from 2023.
New Malware Targeting Developers
Beyond direct attacks on exchanges, Lazarus has deployed specialized hacking tools to target cryptocurrency developers and users. Cybersecurity researchers from Socket have identified six new malicious packages designed to infiltrate development environments, steal credentials, and extract crypto-related information.
These malicious packages target the Node Package Manager (NPM) ecosystem, one of the most widely used libraries for JavaScript application development. Lazarus employs a technique known as “typosquatting,” where they create packages with names similar to popular libraries to trick developers.
One of the identified malware strains, “BeaverTail,” is designed to steal funds from cryptocurrency wallets, with a particular focus on Solana and Exodus wallets. Its activity has also been detected in browsers like Google Chrome, Brave, and Firefox, as well as in key macOS files, allowing credential extraction and sensitive data theft from developers.

Lazarus Continues to Perfect Its Techniques
Although definitively attributing these attacks remains a challenge for cybersecurity experts, the techniques used align closely with Lazarus’s modus operandi. According to analysts from Socket, the use of typosquatting, NPM package attacks, and specific targets within the crypto ecosystem suggests an ongoing and sophisticated evolution in their operational methods.