MetaMask published an article describing a vulnerability in the wallet and the fixes that have been made in the new version. The release notes point out that Halborn researchers showed a case where user keys might have been found unencrypted on disk in rare edge cases, something that has been fixed for MetaMask Extension versions 10.11.3 and higher.
Who Is At Risk?
MetaMask tweeted about the vulnerability:
Security researchers at @HalbornSecurity have disclosed a wallet vulnerability that affects a small segment of users across many browser-based wallets, including MetaMask.https://t.co/2tBl8BfISA
1/ 🧵
— MetaMask 🦊🫰 (@MetaMask) June 15, 2022
“A vast majority of users are *not* at high risk of being compromised due to this, and we have since implemented mitigations for these issues, so these should not be problems for users who are on the MetaMask Extension versions 10.11.3 and later.”
Under the right conditions, security researchers have revealed a method by which a Secret Recovery Phrase found on the hard drive of a compromised computer could be extracted and used to recover a Secret Recovery Phrase for web-based wallets like MetaMask.
As of the time of writing, this issue is not affecting MetaMask Mobile users and only has a marginal effect on MetaMask Extension and other browsers/extension wallet users as well.
As of the version 10.11.3 and later of the MetaMask Extension, mitigations have been implemented, so these issues should no longer be a problem for the 10.11.3 and later users. MetaMask reports that if all three of the following three conditions apply to you, then your hard drive may be at risk:
“The hard drive was not encrypted. You imported your Secret Recovery Phrase into a MetaMask extension on a device that is in possession of someone you do not trust or your computer is compromised. You used the “Show Secret Recovery Phrase” checkbox to view your Secret Recovery Phrase on-screen during that import process.”
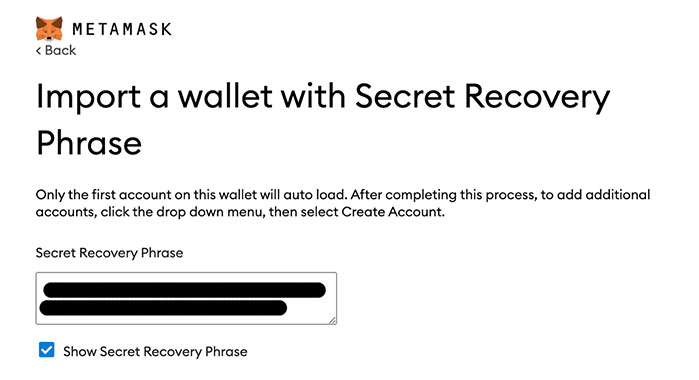
MetaMask users with a compromised device who imported their Secret Recovery Phrase shortly after importing it are most likely to be affected by this vulnerability.
Then you should consider migrating funds from those accounts to another in order to be safe if all of the above conditions apply to you. If all of the above conditions apply to you, then your Secret Recovery Phrase may be accessible to a person who has access to the computer that you imported your Secret Recovery Phrase on.
It is possible for malicious software or hacker to exploit this vulnerability either through physical access to your machine or through malware.
The best course of action for securing your computer against people you don’t trust is to enable full disk encryption on your system if your system is not physically secured. Furthermore, because your funds are managed by hardware wallets, you are not affected by this as well.
As a result, users affected by the use of that Secret Recovery Phrase should consider migrating their funds from those accounts to new accounts created with a new secret recovery phrase.