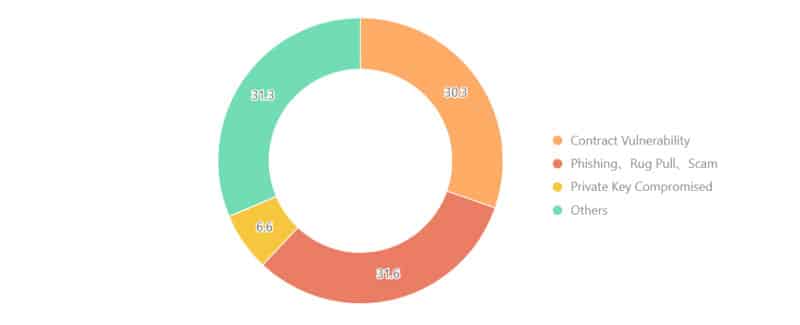
There has been a large number of phishing attacks, rug pulls, and scams in 2022, which can be attributed to almost a third of all recorded blockchain security incidents.
Repeated Methods
SlowMist, a blockchain security firm that has analyzed the data of thousands of victims to identify five common phishing techniques, including malicious browser bookmarks, phony sales orders, and Trojan malicious code spread via messaging apps such as Discord.
There are three types of attack techniques described in the report that can broadly be classified into three categories based on the 303 security incidents reported:
There are various types of vulnerabilities, including those which occur within the project itself due to design flaws, as well as those that result in asset loss as a result of leakage of private keys as a result of rug pulling, phishing, or scamming techniques.
There were a high number of project-related attacks in 2022, most of which stemmed from flaws in the design of the project in the first place, or weaknesses in the contracts. As a result of these attacks, there have been 92 incidents resulting in a loss of nearly $1.1 billion in damages.
With 33 attacks resulting in $348 million in losses, flash loan attacks were the most commonly occurring type of attack, causing the most losses of all the types. There were other kinds of attacks, such as problems with re-entry, price manipulation, and validation issues, among others.
There was only 6.6 percent of instances of private key theft reported, with losses of $762 million as a result.
There are two incidents that have resulted in significant losses due to private key theft. These incidents are Ronin and Harmony, which are both connected to cross-chain bridges.
It is common for users of Web3 applications to have varying levels of security awareness, which has led to a wide range of phishing attacks in the Web3 world.
There have been several instances in the past where hackers have taken control of official social media platforms like Discord and Twitter. For this reason, they are able to impersonate official media accounts and post phishing links such as Mint and AirDrops, sometimes alongside real official content, in order to confuse the public.
In addition to this, analysts also saw that there were some new attack techniques being used in 2022, including malicious attacks on the front end, DNS attacks, and BGP hijackings.
There was an unusual type of attack in which assets were lost as a result of man-made configuration errors resulting in the loss of assets. In conclusion, we can see that in order to prevent these types of attacks and money thefts, an educated person is still the best option.